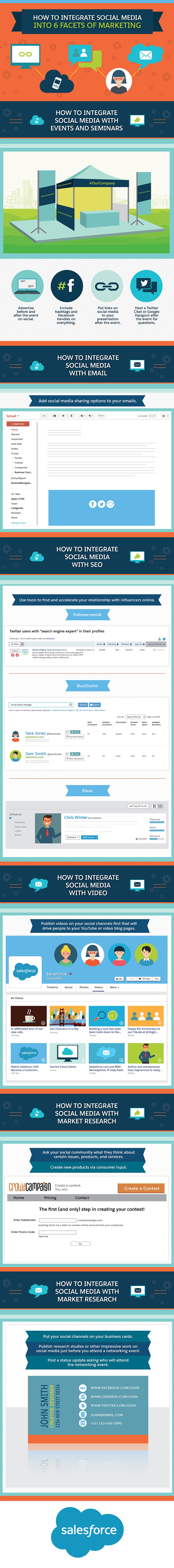
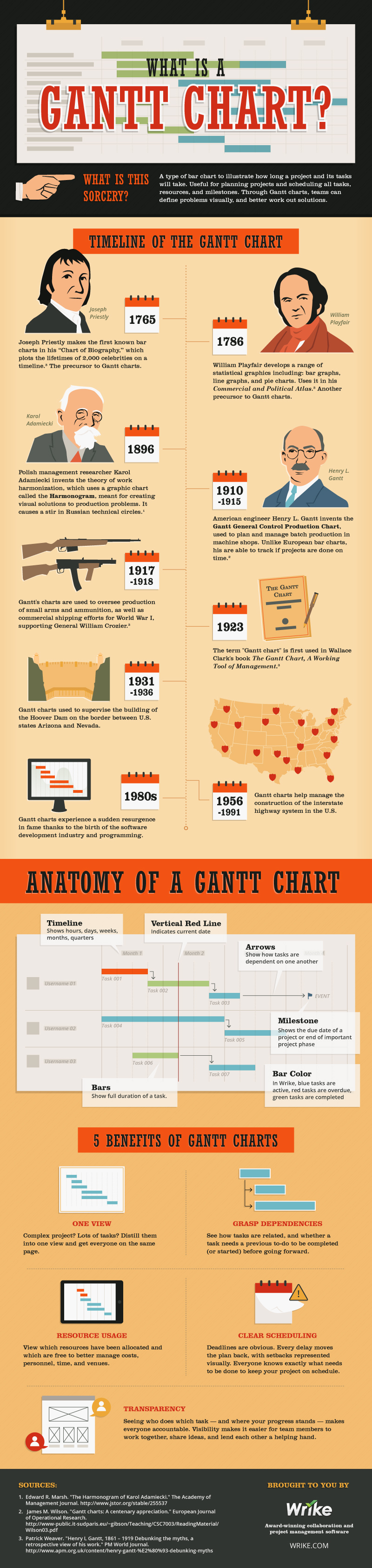
Even as dooms day has been predicted for search marketing, 2016 will present a new approach with the mobility shift - as growing number of individuals and businesses will migrate to native marketing. As 2015 comes to a close, more and more marketing technology companies continue vying for a piece of the pie in the burgeoning mobile market, which hitherto has been dominated by Facebook and Google.
Below are five predictions, distilled from a handful of marketing experts, for trends to watch in 2016.
Re-invention of Social Marketing
As social media adoption reaches its crescendo, a generation shift from how contents are consumed is perhaps more likely, with the likes of Facebook and Twitter losing significant grounds to newer services. Albeit, the user base will continue to grow, Facebook will face huge competition from emerging social networking platforms.
Meanwhile, Instagram has been projected to attain a growth of about 49 per cent in 2016, from the current 32 per cent.
End of the Cookies
Browser-based metrics will gradually be effaced, as the emerging measurement guideline comes to play with the growing adoption of mobile technology. The new formats won't work with cookies and can't be built upon existing legacy Web technologies.
Mobility will drive Visual Social Platforms
Social networking platforms like Instagram, SnapChat and Pinterest will increasingly attract more marketing spends as they'll be naturally appealing to more mobile consumers.
Increasing access to Big Data for Marketing
Brands will be able to incorporate data sets into their marketing campaign strategies with ease, as data exchanges continue to evolve, and will look to share their anonymized user data in exchange for access to the same from other relevant companies.
Native is the new "cool"!
Advertising that matches the platform with which it is delivered is defined as "Native advertising", and often presented in the forms of article, infographic or video, with the specific intent to promote a product, while matching the form and style of the original contents.
For all the hypes around marketing technology, it still doesn't move as fast as you think. Let us know your own predictions in the comment section and at the end of the year we'll see who has the gloating rights!
Below are five predictions, distilled from a handful of marketing experts, for trends to watch in 2016.
Re-invention of Social Marketing
As social media adoption reaches its crescendo, a generation shift from how contents are consumed is perhaps more likely, with the likes of Facebook and Twitter losing significant grounds to newer services. Albeit, the user base will continue to grow, Facebook will face huge competition from emerging social networking platforms.
Meanwhile, Instagram has been projected to attain a growth of about 49 per cent in 2016, from the current 32 per cent.
End of the Cookies
Browser-based metrics will gradually be effaced, as the emerging measurement guideline comes to play with the growing adoption of mobile technology. The new formats won't work with cookies and can't be built upon existing legacy Web technologies.
Mobility will drive Visual Social Platforms
Social networking platforms like Instagram, SnapChat and Pinterest will increasingly attract more marketing spends as they'll be naturally appealing to more mobile consumers.
Increasing access to Big Data for Marketing
Brands will be able to incorporate data sets into their marketing campaign strategies with ease, as data exchanges continue to evolve, and will look to share their anonymized user data in exchange for access to the same from other relevant companies.
Native is the new "cool"!
Advertising that matches the platform with which it is delivered is defined as "Native advertising", and often presented in the forms of article, infographic or video, with the specific intent to promote a product, while matching the form and style of the original contents.
For all the hypes around marketing technology, it still doesn't move as fast as you think. Let us know your own predictions in the comment section and at the end of the year we'll see who has the gloating rights!