While the vulnerabilities affect not only applications running vulnerable libraries, but also services using these applications, organizations may not readily know how widespread the issue is within their environment.
Microsoft’s unified threat intelligence team, have been tracking threats that exploit the remote code execution (RCE) vulnerabilities in Apache Log4j 2 referred to as “Log4Shell” and observed mass scanning by attackers attempting to thumbprint vulnerable systems, as well as scanning by security companies and researchers.
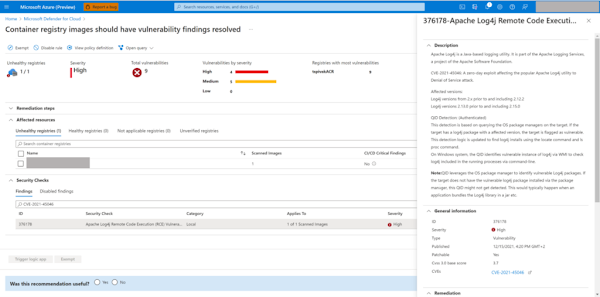
How to Detect and Remediate Vulnerable Apps and Systems?
Microsoft rolled out updates to provide a consolidated view of organizational exposure to the Log4j vulnerabilities on the device, software, and vulnerable component level, through a range of automated, complementing capabilities.
With the Microsoft Defender for Endpoint updates including the following: discovery of vulnerable Log4j library components (paths) on devices, discovery of vulnerable installed applications that contain the Log4j library on devices and dedicated Log4j dashboard that provides a consolidated view of findings across vulnerable devices, software, and files.
These capabilities are supported on Windows 11, Windows 10, and Windows Server 2008, 2012, and 2016; also supported on Linux, but they require updating the Microsoft Defender for Endpoint Linux client to version 101.52.57 (30.121092.15257.0) or later.
Additionally, there is a new schema in advanced hunting, DeviceTvmSoftwareEvidenceBeta, which surfaces file-level findings from the disk and offers the ability to correlate with additional context in advanced hunting of Log4j vulnerabilities. These new capabilities integrate with existing threat and vulnerability management experience and are been rolled out gradually.








No comments