According to Prevailion’s Adversarial Counterintelligence Team (PACT), DarkWatchman uses a robust Domain Generation Algorithm (DGA) to identify its C2 (Command and Control) infrastructure and utilizes novel methods for on-system activity, fileless persistence, and dynamic run-time capabilities like self-updating and recompilation.
The PACT team reverse engineered the DGA and investigated the Threat Actor’s (TA) web-based infrastructure, with consolidated results of their analysis into the report.
What is the Delivery Mechanism and Methodology of DarkWatchman?
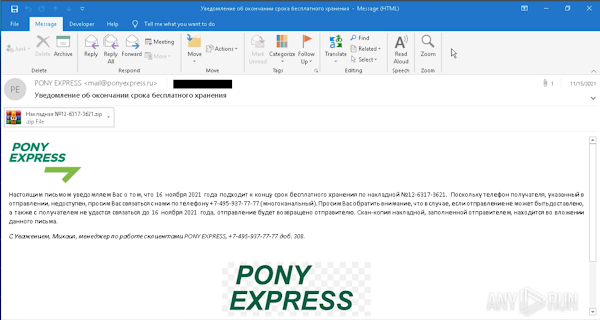
PACT identified full email messages that included intact headers and subsequently a spoofed sender, what's likely the true sender, the intended recipient, the attachment which was identified as the ZIP file containing the malicious logic file that functions as a dropper for the RAT.
The body of the email, contained additional lure material that would likely anticipate after reading the subject, sch as referencing the (malicious) attachment, and claimed to be from Pony Express which further reinforcing the spoofed address.
DarkWatchman utilizes LOLbins and other novel methods of data transfer within modules to avoid detection, with parts of the malware, including configuration strings and the keylogger stored in the registry to avoid writing to disk.
The initial sample analyzed appears to be targeting a Russian-speaking individual or organization, though the script is written with English variable and function names, PACT based on that assesses with moderate confidence that this is an initial access tool for use by ransomware groups or affiliates.








No comments