Docker is a popular service for packaging and deploying software applications; but lately, malicious actors are beginning to target its exposed API endpoints with malware-infested images to mine cryptocurrencies and facilitate distributed denial-of-service (DDoS) attacks.
While the purpose of Docker images is to generate funds by deploying cryptocurrency miner using Docker containers and to distribute these images leveraging the Docker Hub repository, according to Unit 42 researchers.
Docker containers offer a convenient way for packaging software, as evident by its increasing popularity and adoption rate, combined with coin mining capabilities, which makes it a huge target for malicious actors to compute resources for cryptojacking.
How Malicious actors spread the Cryptojacking Malware
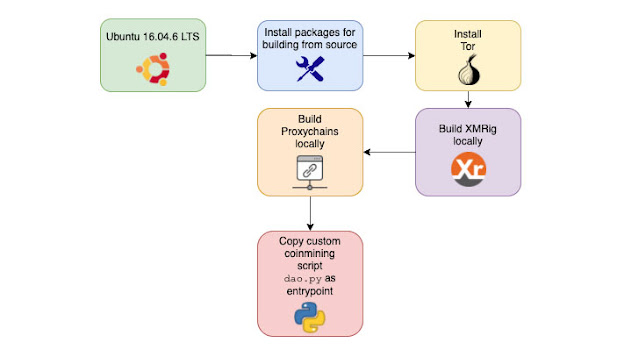
The authors behind the malware images uses a Python script to trigger the cryptojacking operation and takes advantage of network anonymizing tools like ProxyChains and Tor, which enables them to evade network detection.
And the mining code image exploit the infected systems to mine the blocks, using the processing power of the system. With the already taken down Docker Hub account, azurenql, consisted of eight (8) repositories that hosted six malicious images capable of mining the privacy-focused cryptocurrency, Monero.
This particular account have collectively pulled over two million times the images hosted since the start of the campaign in October 2019, and one of the wallet IDs earning more than 525.38 XMR ($36,000).
How to Mitigate against the Cryptojacking Malware
As Docker presents a renown platform-as-a-service (PaaS) solution for Linux and Windows which allows developers to package, test and deploy their applications in a contained virtual environment that isolates the service from the host system.
Therefore, the security best practices recommended are such as: Avoid pulling or using base images from untrusted repositories and install the latest apps and threat definitions on the Networks Firewall.









No comments