The Windows group policy object (GPO) mechanism was reported to have some vulnerability which permits standard user in a domain environment to perform a file system attack, which in turn, allow malicious actors to evade security solutions, and result in severe damage to an organization’s network.
This vulnerability impacts Windows systems, from 2008 or higher and capable of escalating its privileges in a domain environment.
Though, Group Policy updates don't happen in an instant by default, as usually it takes time to propagate over a network, which is more reason Windows includes a tool called GPUpdate.exe for running request on GPO updates from the domain controller.
How the Group Policy vulnerability can be exploited by an attacker
The group policy mechanism is used by admins to enforce policies across a managed environment, allowing admins to essentially do anything they want with GPOs, ranging from disabling Windows Defender and firewall to installing software and printers.
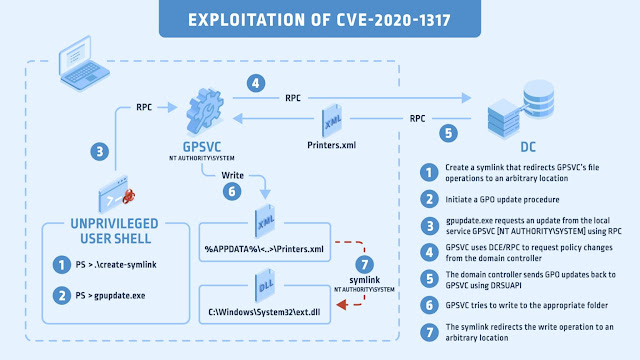
While the Windows’ group policy mechanism is considered a relatively safe way to distribute settings on a domain environment, from printers to backup devices, it needs to interact with many other components. And these many interactions result to potential vulnerabilities.
The bane, however is that a group policy update can be requested manually by a local non-privileged user, which if there is a bug in the group policy update process, can be triggered by an attacker to make a potential attack easier. Instead of having to wait for the 90 minutes (which is the default time period to push group policy updates on a domain environment), an admin could force it immediately.
And the local group policy service, which is named gpsvc, needs to be privileged to carryout its duties, as it runs in the context of NT AUTHORITY\SYSTEM. Therefore, if an attacker manages to find an unsafe file operation, it could easily reparse to another file using a file manipulation attack.
How to mitigate against the risks of the Group Policy vulnerability
The flaw, marked as CVE-2020-1317, affects the most basic mechanisms for centrally managing the settings of Windows PCs and users in Active Directory environments, known as Group Policy.
Microsoft has issued a patch to fix the Group Policy vulnerability that could allow compromised non-privileged user accounts to place malicious DLLs on a system. The company, however failed to disclose further information in its advisory about the severity of the flaw, aside what the researchers from CyberArk who discovered the vulnerability, has already stressed about its seriousness.









No comments