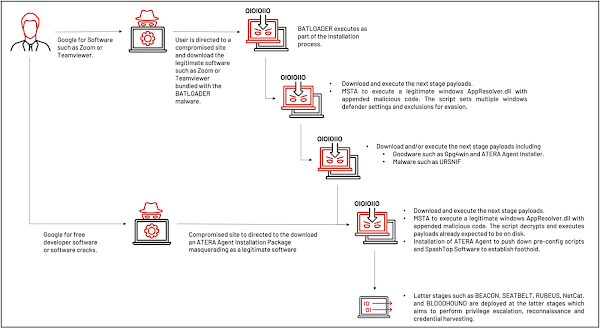
There's an ongoing SEO poisoning attack campaign, according to researchers at Mandiant, that abuse trusted legitimate software utilities to trick web users into downloading the infamous malware, BATLOADER, on their machines.
The team also observed a crafty defense evasion technique employed by the hackers using mshta.exe, a Windows-native utility designed to execute Microsoft HTML Application (HTA) files.
How Hackers use SEO Poisoning to Distribute BATLOADER malware?
In the SEO poisoning campaign, the hackers often use “free productivity apps installation” or “free software development tools installation” as keywords to lure unsuspecting users to a compromised website to download a malicious installer.
While the installer contains a compromised version of the legitimate software bundled with the BATLOADER malware, and the malware is executed during the software installation process. This initial phase is the beginning of a multi-stage infection chain which provides the hackers with a strong foothold within the target organization.
And such legitimate tools as Msiexec.exe, PowerShell, and Mshta.exe allow proxy execution of the malicious payloads which enables the hackers to avoid detection.
How to Mitigate against SEO Poisoning Attack?
The public release of this information, means that other unaffiliated threat actors would be replicating the techniques for their own malicious motives and objectives.
Therefore, organizations are recommended to follow a holistic security system that mapped to the MITRE ATT&CK framework and includes related intelligence so they can take decisive action throughout their environment.








No comments