The researchers at Promon, a Norwegian cybersecurity company has unveiled details of a new critical vulnerability (CVE-2020-0096) affecting almost all the Android operating system versions that could allow attackers to carry out a more sophisticated Strandhogg attack.
While Strandhogg attack was a security vulnerability that affects Android devices which malicious apps can exploit by masquerading as legitimate apps installed on a target device to display fake interfaces and tricking users into giving out their sensitive account information.
Now, the current strain of the vulnerability is dubbed 'Strandhogg 2.0' and affects all Android devices, except those running Android 10, which unfortunately, is only running on about 15 - 20% of the total Android-powered devices, leaving billions of smartphones vulnerable to the attack.
How the Malware has evolved from StrandHogg 1.0 to 2.0?
The malware, StrandHogg 1.0 resided in the multitasking feature on Android, whereas the new strain, Strandhogg 2.0 is an elevation of privilege vulnerability that allows attackers to gain access to almost all Android apps.
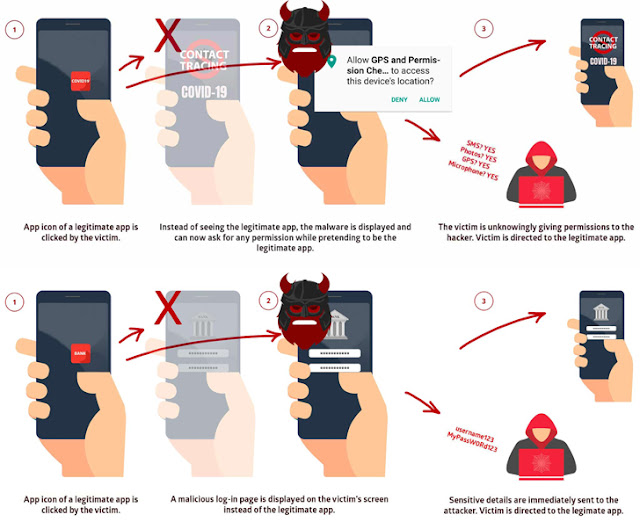
If a device is infiltrated, once a user taps the icon of a legitimate app, the malware exploits the Strandhogg vulnerabilities to intercept and hijack this activity to display a fake interface to the user instead of launching the actual application. But, unlike StrandHogg 1.0 which only attacks one app at a time, the latest vulnerability could allow attackers "dynamically attack nearly all apps on a given device simultaneously at the touch of a button," without requiring a pre-configuration for the targeted apps.
With StrandHogg 2.0, attackers can gain access to private SMS messages and photos, or even steal victims' login credentials, including online banking accounts; make and/or record phone conversations, and spy through the phone's camera and microphone.
How to Mitigate the Risks of the Malware
StrandHogg flaws are potentially dangerous, and besides stealing users login credentials through a convincingly fake UI screen, the malware can also escalate its capabilities by tricking users into granting it sensitive permissions while posing as a legitimate app.
And StrandHogg 2.0 will also be harder for any anti-virus or security scanners to detect, as such, it poses a significant danger to Android users. Albeit, the researchers had responsibly reported the new vulnerability to Google since December last year.
Google subsequently pushed out a patch for it in April 2020, but with the delays in compliance on the part of smartphone manufacturing companies, who have only started rolling out the software updates to their respective users for this month.
Therefore, if you wish to safegurad your device, prior to getting the security patch, keep an eye on permission popups that don't contain an app name, or permissions asked from an app that shouldn't need the permissions.









No comments